- Key insight: Financial institutions paid more in ransom to cybercriminals than any other sector, accounting for $365.6 million across 432 incidents.
- What’s at stake: Banks navigate a “dual reality” as both prime targets for extortion and the government’s primary tripwire for detecting illicit payments.
- Supporting data: Bitcoin remains the overwhelming currency of choice for extortionists, accounting for 97% of reported ransomware transactions.
Overview bullets generated by AI with editorial review
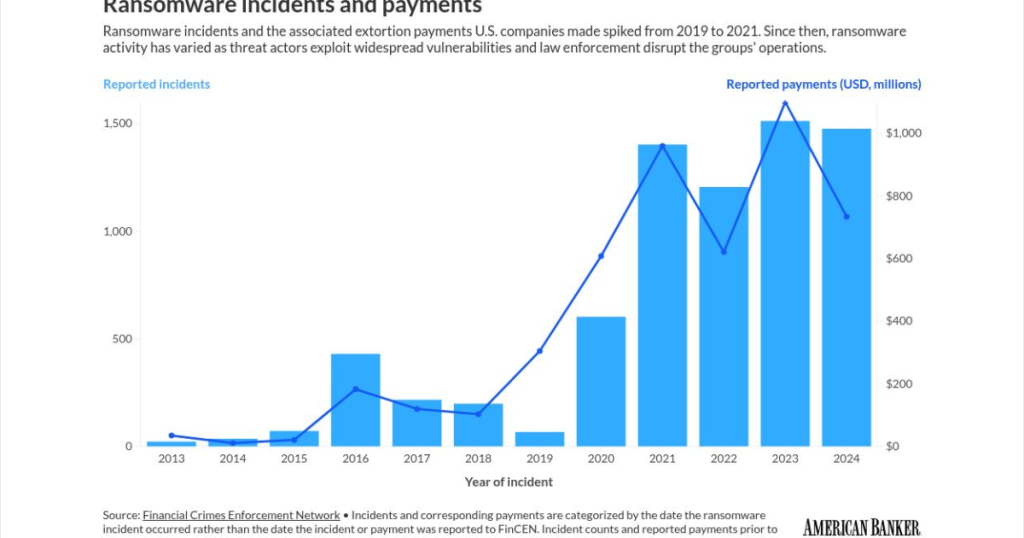
Ransomware payments reached approximately $1.1 billion in 2023 before retreating significantly to $734 million in 2024, following high-profile law enforcement disruptions of cybercriminal activity.
In
FinCEN attributes the decline in extortion payments in part to successful federal and international law enforcement disruptions of major ransomware groups, including ALPHV (also known as BlackCat) and
Despite disruptions, FinCEN noted that ALPHV was the most impactful ransomware during the two-year review period, generating $395.3 million in payments.
A bank reports a ransomware payment to the Treasury Department when it knows or suspects such a payment is related to ransomware. Although aggregate payments declined, the total number of such reports remained relatively flat from 2023 to 2024, hovering around 1,500 annually.
For the banking sector, the data presents a stark dual reality: banks serve as the primary tripwire for detecting both ransomware payments and money laundering that follows these payments, but they are also top-tier targets for ransomware gangs.
With median ransom payments fluctuating between $124,000 and $175,000 over the last three years, and demands often reaching into the millions, the financial stakes for banks — both as gatekeepers and victims — remain high.
During the two-year period FinCEN analyzed (January 2022 to December 2024), the manufacturing sector experienced the highest volume of individual incidents (456). However, the financial services sector paid the most to cybercriminals.
Financial institutions accounted for approximately $365.6 million in total payments across 432 reported incidents during the review period, surpassing healthcare and manufacturing.
Not all ransomware incidents become public knowledge. Paying the extortion fee during a ransomware incident can help a company prevent the stolen data from becoming public, though this requires the cybercriminals to maintain their promise.
However, the FBI discourages ransomware victims from making such payments, as they help to fund and incentivize the illegal activity.
The U.K. National Crime Agency has also warned it has found LockBit retaining data belonging to victims who had paid a ransom to the threat actors. The agency has used these findings to argue that, “even when a ransom is paid, it does not guarantee that data will be deleted, despite what the criminals have promised.”
Indeed, not all ransomware victims make extortion payments. In one highly visible case this year, LockBit
Compliance obligations and red flags
For anti-money laundering and Bank Secrecy Act officers, the FinCEN report this week also underscores the necessity of precise reporting.
FinCEN advises that financial institutions should include the key term “CYBER-FIN-2021-A004” in suspicious activity reports to flag a connection to ransomware.
Furthermore, the agency urged compliance teams to include so-called “Indicators of Compromise” directly in the BSA reporting form. These include suspicious email addresses, file names, hashes, domains and IP addresses. Indicators of compromise often help other companies detect similar intrusions.
When monitoring transaction flows, bankers should note that Bitcoin remains the overwhelming currency of choice for extortionists. Bitcoin accounted for 97% of reported ransomware transactions, according to FinCEN, while privacy coins such as Monero appeared in only 2% of reports.
Additionally, threat actors continue to launder their ransomware proceeds primarily through unhosted crypto wallets, which are digital wallets that owners manage directly rather than managing through, say, a cryptocurrency exchange.
Some of these findings could be skewed by underreporting due to difficulties with monitoring for and identifying such transactions, FinCEN warned.
“The data in this report consists only of information received through BSA reporting and is not a complete representation of all ransomware attacks or payments during the review period,” the report reads.
Scrutiny over ransomware payments
Although federal prosecutors generally do not target companies that pay ransomware payments, and the practice is generally regarded as legal in some circumstances, it is under intensifying scrutiny.
The U.K. Home Office is currently consulting on legislative proposals that could ban ransomware payments for all public sector bodies and critical national infrastructure providers. While the effort is currently limited to the U.K., it signals a potential shift in the global regulatory landscape that multinational banks must monitor.
Bankers in the U.S. must also remain vigilant regarding strict liability for sanctions violations. FinCEN advised institutions to contact the Office of Foreign Assets Control immediately if there is any reason to suspect a cyber actor demanding payment is a sanctioned entity.
“We will continue to work closely alongside our partners, across the U.S. government and around the world to disrupt cybercrime operations… and to find and hold accountable those responsible for them,” Attorney General Merrick Garland said in a May press release regarding charges against the LockBit administrator.
For the time being, banks are encouraged to continue reporting ransomware payments made either by the bank itself or by its customers.
Andrea Gacki, the director of FinCEN, said financial institutions “play a key role in protecting our economy from ransomware and other cyber threats.”
“By quickly reporting suspicious activity under the Bank Secrecy Act, they provide law enforcement with critical information to help detect cybersecurity trends that can damage our economy,” Gacki said.